With the popularity of Office 365 and SharePoint Online on the rise, scammers are taking advantage of its prevalence and using the platform as a way of phishing for confidential data such as usernames and passwords.
Cloud Security firm Avanan recently discovered a particularly devious scam that uses genuine SharePoint Online sharing invitation emails as a platform for delivering malicious links to unsuspecting users.
Download our spam email checklist, so you're never caught out again
How does the scam work?
•A user receives a SharePoint Online sharing invitation via email that provides a link to a file in another user’s SharePoint Online account. At this stage, the email received by the user is a genuine email that has been generated by SharePoint Online, so goes undetected by any spam email filters.
•The user clicks the link in the email which takes them to the shared file in the scammer’s SharePoint Online account.
•The shared file, most likely a Word document, contains Microsoft imagery along with an additional link titled, “Access Document”.
•This “Access Document” link is clicked by the user, which then takes them to a non-genuine login screen that looks just like a Microsoft or Office 365 authentication page, but is actually a mimicked (or “spoofed”) page.
•Now the user fills in their Office 365 email address followed by the associated password, with these details being submitted to the scammer and not, as the user is expecting, to Microsoft.
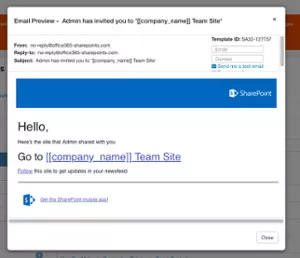
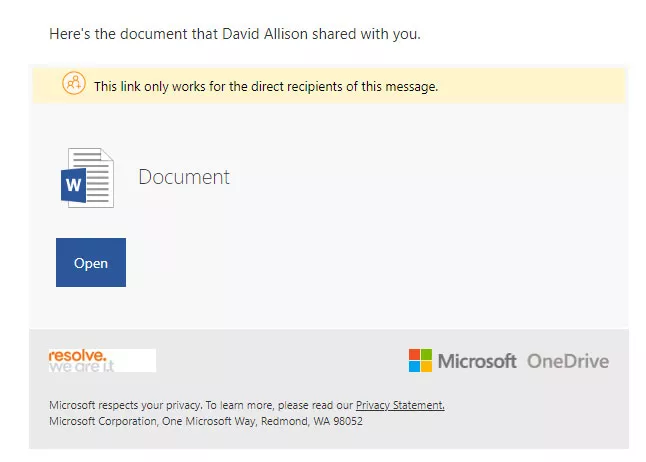
What do the SharePoint Online sharing emails look like?
The first image below is a screenshot of the email originally shared by Avanan, followed by other examples of invitation emails:
Screenshot provided by Avanan:

Two further examples of sharing emails:
How do I know if the email I have received is from a scammer?
There are certain hallmarks of phishing emails to look out for, and I covered a whole host of these in my previous blog, 9 Tips to Help Identify Phishing Emails. But, the first question you should ask yourself upon receiving this kind of sharing invitation email is, “am I expecting to receive an invitation to a shared document or folder?”. If not, then check the name of the sender or the company in the body of the invitation email. If you do not recognise this person, immediately delete the email from your Inbox and deleted items area.
What is the genuine process of viewing a shared document from SharePoint Online and what does this look like?
If someone was sharing a document with you in this way, they may well explain the process to you, but just so that you are aware, the process goes like this:
1. You receive the usual genuine sharing invitation email in exactly the same way, with the name of the person who shared it visible on the invitation.
2. You click the link or button in the email to view the file.
3. Now one of two things will happen, depending on how the user shared the document with you:
a. You will be asked to enter the email address the invitation was sent to
OR….
b. You will be taken directly to the document that was shared with you.
4. If (a) is the result of clicking the link or button, then the user has shared the document and specified that additional verification must be entered (note that you have been taken directly to the login page, unlike the scam invitation which required you to click an additional link called “Access Document” before logging in).
5. If (b) was the outcome, then the sender has used “anonymous” sharing to share the document, in which case you are not required to log in at any stage.
Any more advice on this kind of attack?
If you don’t recognise the sender, ask another member of your team to see if they are aware of any external users who are wanting to share documents with you. Even if you do recognise the sender, just contact them to check that they have recently initiated the sharing invitation, just in case they have been spoofed.
The key here, as with any other type of unusual looking email, is to always be vigilant and question any email that you do not recognise, especially one that has links to external websites or resources. Download the checklist below so you can run through it every time you receive a questionable email.




