We live in a digital age where emails are a vital part of communication. With a big increase in receiving information instantly, as well as rising concerns in saving the planet, physical letters are becoming less common with businesses, banks and the general workplace. Unfortunately, not every email you receive will be friendly.
Phishing attacks are emails that are designed to trick you into revealing sensitive information, such as personal details, bank details and passwords.
In this blog, we’ll teach you how to outsmart cybercriminals and keep safe from their tricks. It doesn’t matter if you send hundreds of emails a day or a week, by the end of this blog you’ll know how to avoid becoming a cyberattack victim.
What is a phishing attack?
A phishing attack is an online trick used by cybercriminals. They pretend to be someone they aren’t, such as your bank, social media or even your boss and send you a very realistic-looking email. They can “phish” your details by getting you to click a link or open an attachment. This can lead to what appears to be a login page for a service that asks you to type in your personal details. Alternatively, an attachment can hold a virus or malware that infects your device once opened.
How to spot a phishing email attack
We know this can sound scary, but we have curated a list of ways to spot a phishing email and keep you and your details safe from cybercriminals.
Unusual or Inaccurate Display Name
A popular phishing tactic is to “spoof” the display name that is presented against an email address. Spoofing is the process of making an email look as if it’s from a genuine sender by masking the cybercriminal’s email address with a display name that suggests a genuine company (such as amazon.co.uk). An example email may look like the below:
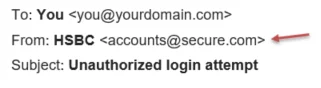
So, although the display name shows as “HSBC”, the email address itself suggests that the email has not come from HSBC. Your email client, such as Outlook, should provide a way of checking the email address behind the display name. This can be achieved by clicking the bold sender name to reveal the actual email address it was sent from.
Review any links before clicking
Sometimes a phishing email will include one or more links in the body of the email. If you are unsure of any links, don’t click them to test – simply copy and paste or manually type the address into a website address analyser, such as the one on VirusTotal’s website.
Spelling mistakes or bad grammar within the email
A classic tell-tale sign of a phishing email is the presence of a number of spelling and / or grammar mistakes that are littered throughout the email. A high-profile company such as HSBC or Amazon is highly unlikely to have any mistakes in their emails, whereas a cybercriminal is more likely to create mistakes from rushing to write a generic email that they can mass send, possibly having a language barrier or using AI generative techniques that may write in “American grammar” with the intention to send to the UK and vice versa.
Review the email’s salutation
Check how the email has been addressed to you. Legitimate companies will address you by your first and / or last name, so be on the lookout for any emails that start “Dear Valued Customer” or “Dear Sir / Madam”. Most phishing emails are sent to hundreds and thousands of people at once, therefore there isn’t normally any personalisation which can specify a gender or age.
Asking for personal information
No genuine email from a large company would request that any personal information be sent in an email, so any email making this request should always be ignored.
In the email, they may ask for you to send your card or bank details, or they may ask for you to reply with personal information such as your date of birth.
If you receive an email from a large company asking for this information, it is best practise to call the company and confirm this. Make sure you Google the phone number to call instead of a phone number listed on the suspected email as it may not be the correct one for the business.
Look out for urgent or immediate action
Cybercriminals will use fearmongering tactics to invoke a response from unwitting victims, so be on the lookout for any phrases such as, “Immediate action required to prevent account closure” or “Your account has been suspended”.
This is a common tactic as they try and pressure you to do things before fully sitting back and thinking about it.
One example of this could be from a social network stating your account is going to be deactivated if you don’t log in immediately. The link they then present on the email could be for a spoof website that looks almost identical to that social network’s login page. They will then present you an email or username box and password box and wait for you to fill it in, capturing your login details.
Inspect the signature
A lack of a signature at the end of an email can be a clear indication that the email is disingenuous.
Legitimate companies will include contact details on their emails, such as phone numbers, website addresses, and links to their social media and logos.
Receiving an email with no signature and just a name or company is a big red flag, the majority of emails from employees of a company will have an on-brand signature.
There may be a signature at the bottom of the email, but there could be tell-tale signs that it is not legit. The logo may be different, the text could be the wrong colour or font, or it may be that there are spelling mistakes, giving away that it isn’t from the company it is pretending to be.
Unusual Attachments
It isn’t just links you have to be aware of when it comes to phishing emails – attachments can have just as much, if not more of a risk.
If a PDF is attached to the email, and you download it to view it, it could be a virus you are downloading instead. These attachments can be disguised as invoices, wage slips or documents.
A particularly risky download is ransomware, which has been on the rise in recent years and can cause massive amounts of disruption to businesses. Ransomware encrypts all your data and cybercriminals request large amounts of money to retrieve it. Not having your data backed up could mean a permanent loss for your business. Read more about how Resolve can help your business with backup IT security today.
Don’t trust the email’s “header”
If you have spotted one or more of the traits of a phishing email but see that the display name matches the email address in the email’s “header”, even the email address can be spoofed so it can’t always be trusted.
Spotting a phishing email is not always easy, but they can often be stopped before they reach your inbox. Resolve can provide a number of solutions that help block malicious emails, including an offering from Microsoft called Office 365 Advanced Threat Protection.
Train your staff to spot phishing attacks today
One of the biggest threats to your business can be untrained staff. With phishing emails becoming more convincing all it can take is one member of your staff to click a link or download an attachment to put your company at risk.
Resolve offers a KnowBe4 security training for staff which assesses your staff’s awareness, educating them on how to spot phishing emails and sends “fake” phishing emails periodically. This helps you to know where more training is needed. It is much better for your company to fall victim to a “fake” phishing email and be able to learn from it, rather than falling victim to a malicious email from a cybercriminals!
Conclusion
The best defence against cyber criminals is knowledge. Once you know how to successfully spot signs of a phishing attack you are one step closer to not becoming a victim of one.
We'd recommend downloading the checklist below, so you can run through it every time you think you've received a spam email. Of course, if you feel you are suffering as a result of spam emails, please contact us and we will help you discuss your options.
Download our spam email checklist, so you're never caught out again




