This guide will demonstrate how to configure a point-to-site configuration within Azure, and how to deploy this out to users automatically via Group Policy.
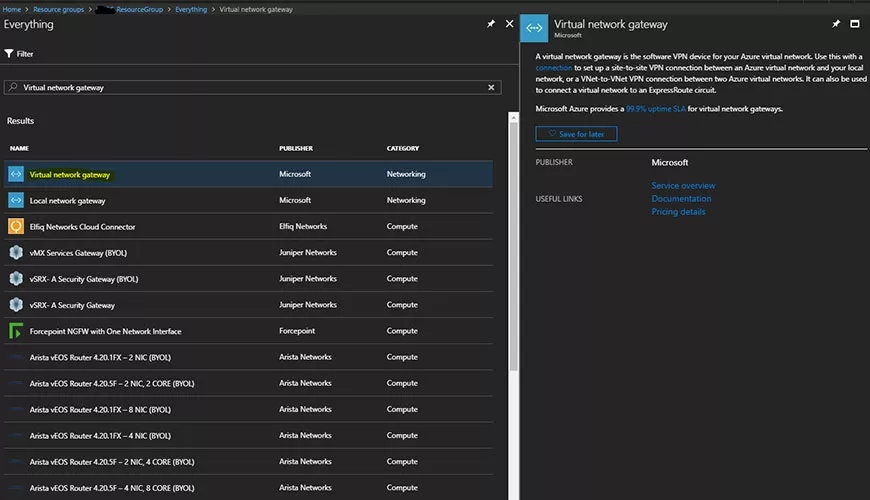
1. Log into the client’s Azure portal, go to ‘Resource Groups’ and choose the resource group which contains the virtual network you would like the client VPN to connect to.
2. The virtual network will require a virtual network gateway to provide the functionality of configuring a point-to-site VPN connection. If the resource group does not contain a virtual network gateway, click ‘Add’ and search for ‘virtual network gateway’. Click ‘Create’ and configure accordingly. (If your resource group already contains a virtual network gateway, skip to step 3.)
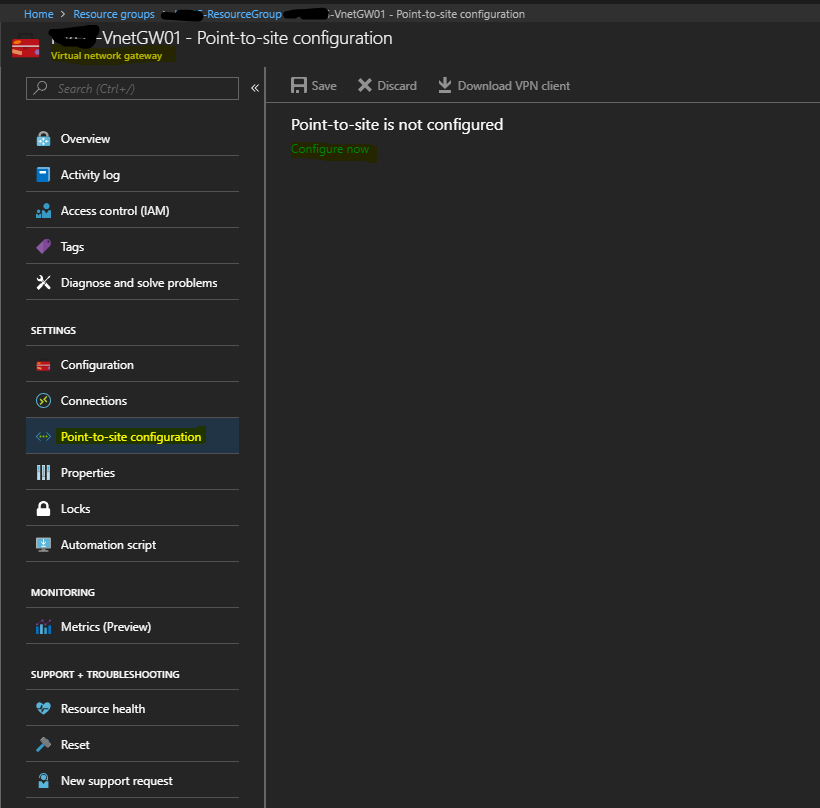
3. Once the Virtual Network Gateway has been configured, you will see this displayed within your resource group. Click on this to open the blade for configuration. Go to Point-to-site configuration to begin the configuration.
4. First, we shall need to generate certificates used for client authentication (this is a self-signed root certificate which is imported into Azure, which then uses a child certificates for user authentication).
From a Windows 10 machine, run the following command in an elevated PowerShell window (do not close the window):
$cert = New-SelfSignedCertificate -Type Custom -KeySpec Signature `
-Subject "CN=P2SRootCert" -KeyExportPolicy Exportable `
-HashAlgorithm sha256 -KeyLength 2048 `
-CertStoreLocation "Cert:CurrentUserMy" -KeyUsageProperty Sign -KeyUsage CertSign
5. Now that we have generated a root certificate on a Windows 10 machine, we need to make sure this is kept safe by exporting the certificate to a PFX file (make note of the PFX password). More information on how to do this can be found here: https://support.microsoft.com/en-us/help/823503/how-to-import-and-export-certificates-so-that-you-can-use-s-mime-in-ou
6. Using the same elevated PowerShell window from the previously used Windows 10 machine used to generate the root certificate, we shall create a child certificate using the below command:
New-SelfSignedCertificate -Type Custom -DnsName P2SChildCert -KeySpec Signature `-Subject "CN=P2SChildCert" -KeyExportPolicy Exportable `-HashAlgorithm sha256 -KeyLength 2048 `-CertStoreLocation "Cert:CurrentUserMy" `-Signer $cert -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.2")
7. This command will have generated a child certificate on the Windows 10 machine, which now needs to be exported to a PFX file using the same process used in Step 5. (remember to make note of the PFX password).
8. You should now have a folder with both the root and child certificates as a PFX file, with a text file containing the passwords for each certificate. Copy this folder to the client’s DC (rename the folder ‘AzureP2S’), from here we shall import the root certificate to the DC’s personal store. (more information can be found on how to import certificates here.)
9. Once you have imported the root certificate into the DC’s personal store we need to export the root certificate again from here, however this time specify the ‘do not export the private key’ option. Choose ‘Base-64 encoded X.509’ for the file format and save the file to any chosen location with any name.
10. Locate the exported file and open with notepad, this will display the certificate in text format, highlight the text between the ‘begin’ and ‘end’ and copy the text.
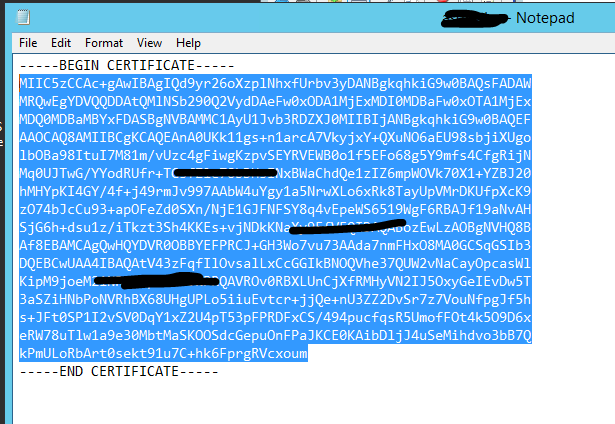
11. Back in the Azure portal, paste the copied certificate text into the point-to-site configuration section of the Virtual network gateway. The field which you need to paste into is ‘Public certificate data’. Give this a useful name.
12. Specify an address pool within the point-to-site configuration, this needs to be separate to the existing VNET subnet, so if the existing subnet is for example ‘192.168.1.0/24’, use another subnet such as ‘192.168.10.0/24’.
13. Click ‘Save’ to complete the configuration of P2S within the Azure portal.
14. Once the P2S configuration has completed, you should have the option to ‘Download VPN client’. Click on this and extract the downloaded zip file.
15. Locate the ‘WindowsAmd64’ folder and run the ‘VpnClientSetupAmd64’ exe file. This will configure the Azure VPN on your machine, whilst this is an easy method to connect to the Azure VPN it may not suit the client as this process requires manual interaction. For group policy we need to create the VPN using alternate methods.
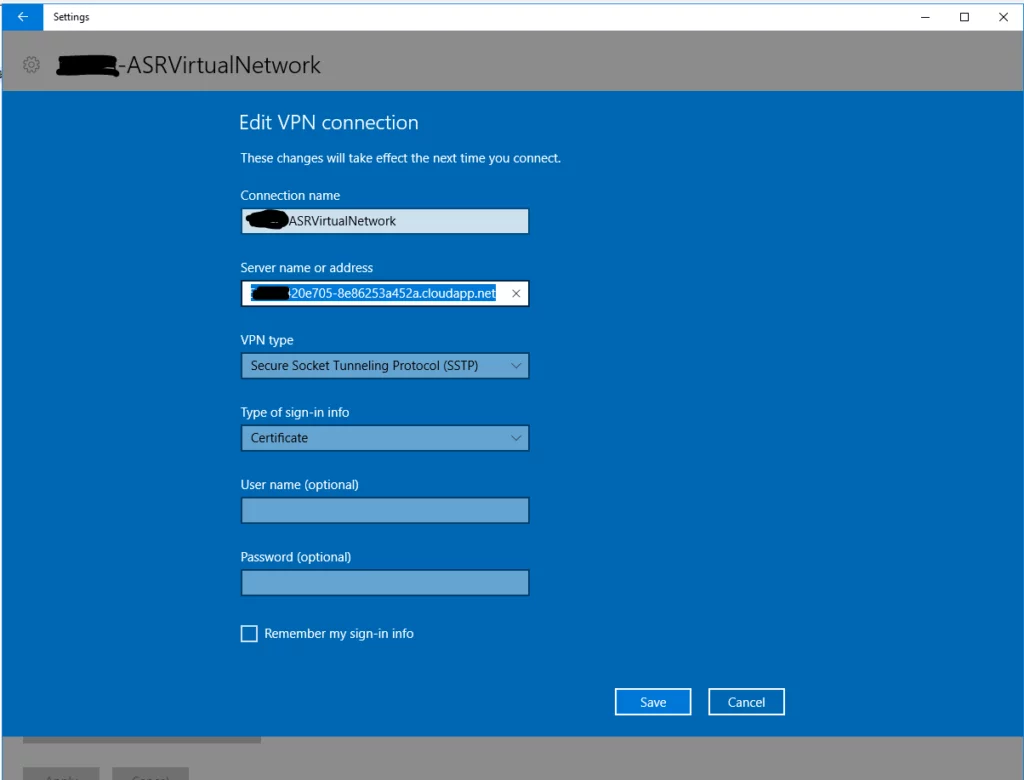
16. Go to VPN settings on your PC and locate the new Azure VPN. Click ‘Connect’ to connect to the VPN. Once connected click on the VPN again and then click ‘Advanced options’.
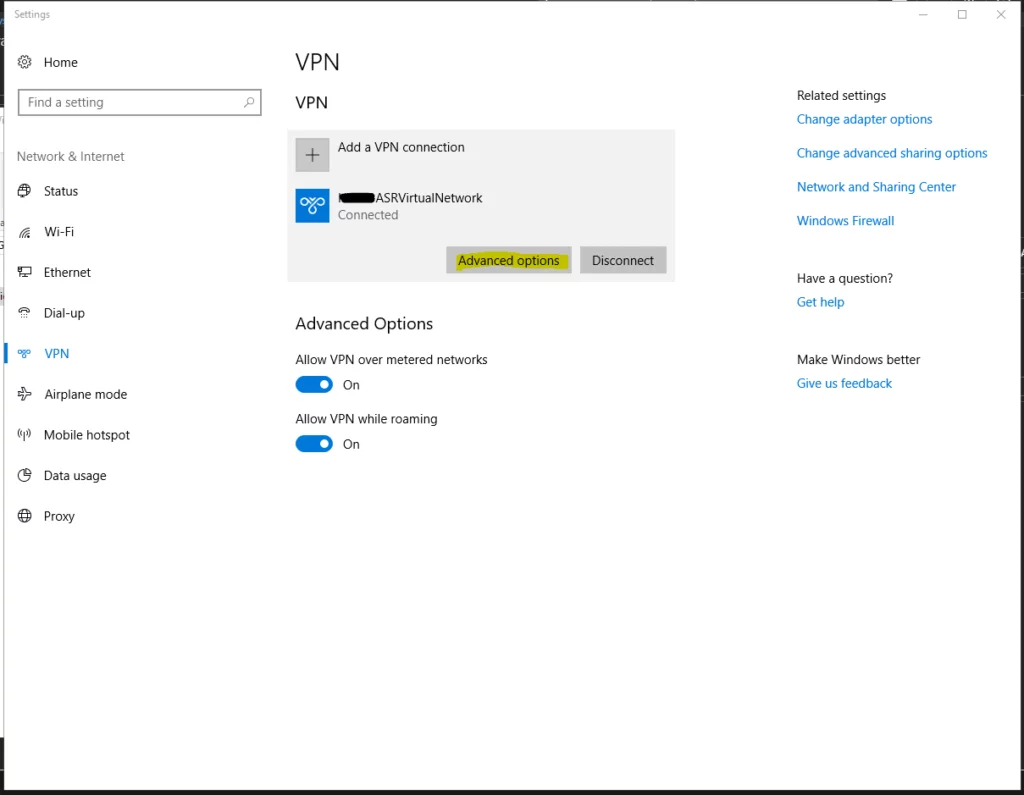
17. Within the advanced options, click ‘Edit’ and copy the ‘Server name or address’ field. (you won’t need this now, however store somewhere for use in the later steps.)
Now that we have configured the P2S settings with both root and child certificates generated for authentication, we now need to configure the client-side VPN, so users can connect from their machines. To do this we shall deploy the child certificate via Group policy using a PowerShell script. Below is a step by step guide on how to configure this.
18. In the previous step 8, we had a folder which contained both the root and child certificate, alongside a text file containing the passwords. You can download the script from the following link: http://resolve.co.uk/assets/downloads/Azure%20P2S%20Client%20VPN%20Setup.zip. Copy this script file into the ‘AzureP2S’ folder on the Client’s DC.
19. Share the ‘AzureP2S’ folder on the network with ‘Everyone’ full control permissions.
20. Edit the PowerShell script using PowerShell ISE, where we shall be adjusting the highlighted sections appropriately:
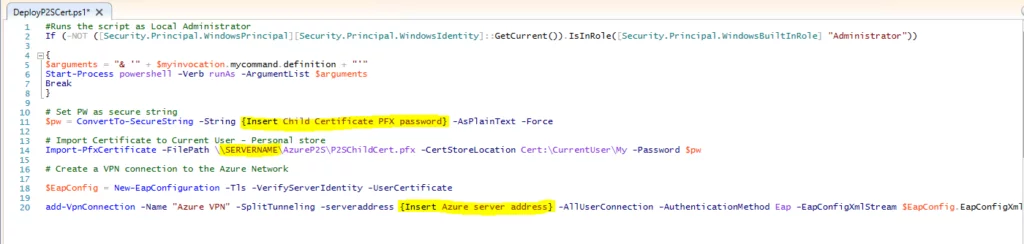
{Insert Child Certificate PFX password}
This section we need to specify the password assigned to the Child certificate PFX file as per step 7.
\SERVERNAME
This section needs to be changed to the name of the server where the PFX file is stored e.g. TEST-DC01
{Insert Azure server address}
This section requires the Azure server address copied in step 17.
21. Once you have adjusted the script accordingly, it should look something like this:
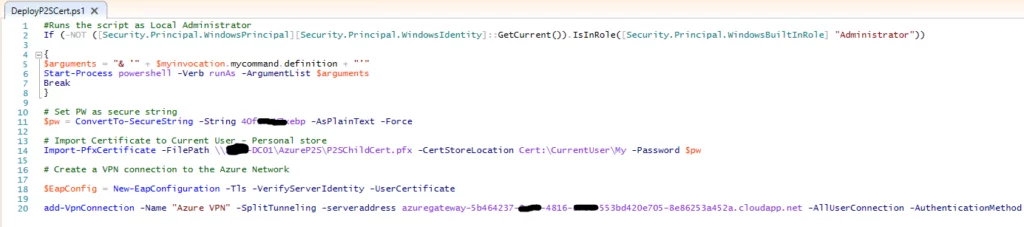
22. Now we need to deploy this script via group policy, to do so create a new group policy object called ‘Deploy Azure P2S VPN’ and edit with the following settings:
Allow PowerShell scripts to execute on the machine:
Computer configuration > Policies > Administrative Templates > Windows Components > Windows PowerShell > Turn on Script Execution: Enabled (specify ‘Allow local scripts and remote signed scripts’ for the execution policy)
Specify the PowerShell script to run on Logon:
User Configuration > Policies > Windows Settings > Scripts > Logon
Within the ‘Logon Properties’ window go to the ‘PowerShell Scripts’ tab. Within here click on ‘Show Files…’ and copy the script from the ‘AzureP2S’ folder into this GPO folder. Then click ‘Add…’ and type the following for Script name and parameters:
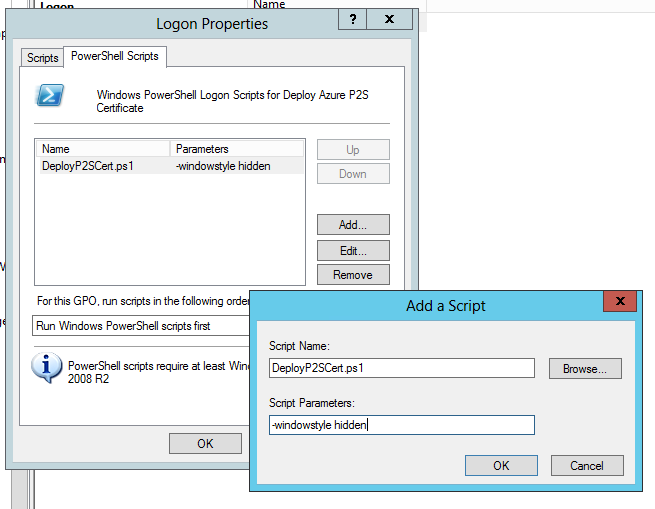
23. Once you have configured the GPO with the settings mentioned, OK all windows and close the ‘Group Policy Management Editor’ window.
24. Highlight the newly created GPO and drag to the relevant user OUs within the organisation where you would like the Azure VPN to be deployed to the users.
This process should now have created a group policy which runs the edited script to deploy the Azure VPN using the child certificate we created. The next time user’s login to their machines they should see the ‘Azure VPN’ display within their network settings, and can simply click ‘connect’ to gain a connection the Azure network.
For more information on how to configure a Point-to-Site VPN, see the Microsoft doc link below:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-point-to-site-resource-manager-portal
For more information on creating root and child certificates, see the Microsoft doc link below:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-certificates-point-to-site#clientcert
http://resolve.co.uk/assets/downloads/Azure%20P2S%20Client%20VPN%20Setup.zip